Table of Contents:
- Introduction (1/12)
- The Easy Way (2/12)
- Basics (3/12)
- Debugging (4/12)
- Hooking Winsock (5/12)
- Egress – Walking the Call Stack (6/12)
- Egress – Reversing the Request Encrypt Function (7/12)
- Egress – Monitoring (8/12)
- Ingress – Walking the Call Stack (9/12)
- Ingress – Reversing the Response Decrypt Function (10/12)
- Ingress – Monitoring (11/12)
- Conclusion (12/12)
- Source code
This post starts off the series by showing the easy way to reverse engineer REST APIs: by simply looking at the request and response flow. To start, we will launch the game and use Wireshark to look at the traffic going over the wire. In order to filter out the traffic, we need to find out what IP(s) the game is connected to. After launching the game and running netstat, we get the following output:
netstat -n -p TCP -b
...
[RelicCardinal.exe]
TCP 192.168.0.153:52322 52.186.164.33:443 ESTABLISHED
[RelicCardinal.exe]
TCP 192.168.0.153:52323 52.186.164.33:443 ESTABLISHED
[RelicCardinal.exe]
TCP 192.168.0.153:52324 23.200.0.183:443 ESTABLISHED
[RelicCardinal.exe]
TCP 192.168.0.153:52329 52.165.184.209:443 ESTABLISHED
[RelicCardinal.exe]
TCP 192.168.0.153:58611 52.226.139.185:443 ESTABLISHED
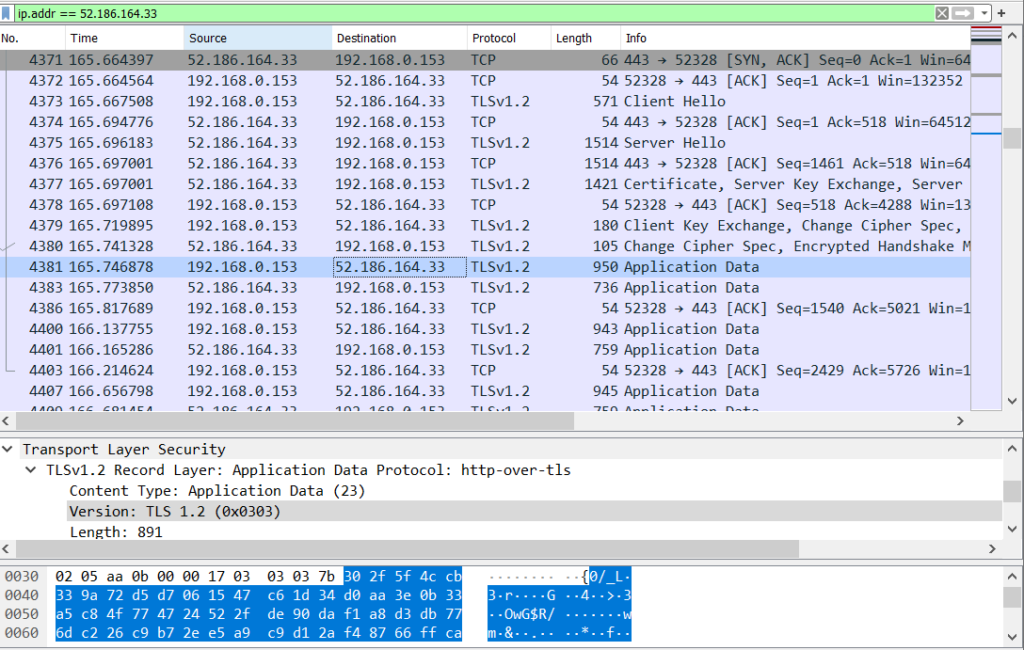
...The game is connecting on port 443, which means that communication is happening over TLS. Looking at Wireshark, there is no useful data to be seen since everything is encrypted. At best you can extract the hostname information from the server name indication extension of TLS, though useful information like query strings and content bodies will still remain encrypted.
This is a minor inconvenience, but still an inconvenience nonetheless. To get at the decrypted data requires a few more steps: first, we need to set up a proxy that intercepts traffic over HTTPS, then we need to run the game through this proxy.
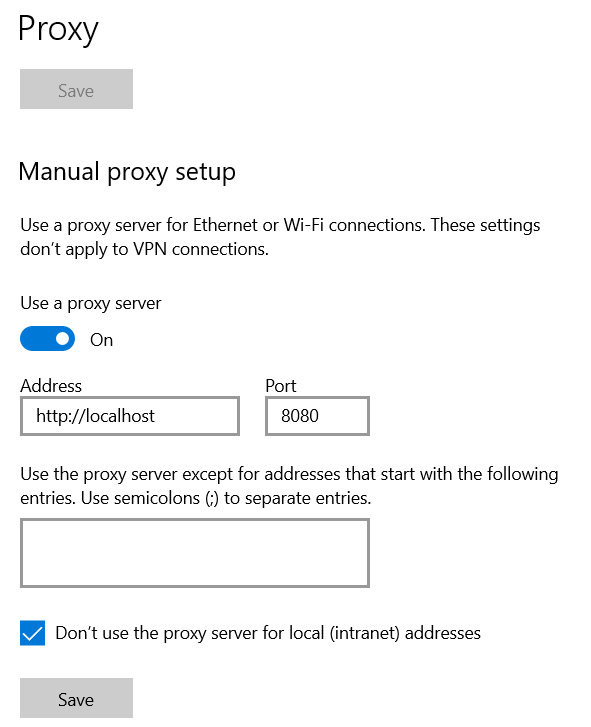
Setting up a HTTPS proxy is pretty straightforward: mitmproxy can be used for this. After installing the tool, navigate to the Windows Proxy Settings and add in a proxy running on localhost:8080
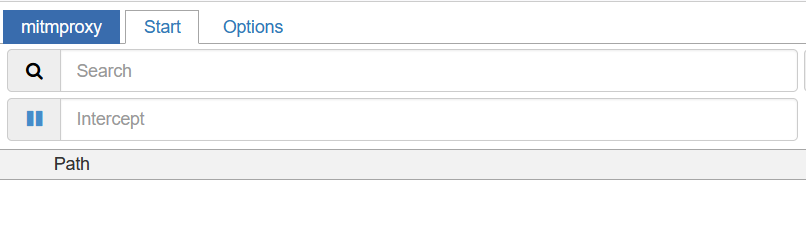
Once this is done, you can launch mitmweb.exe from the mitmproxy installation directory. After launching mitmweb.exe, a new browser tab should pop up showing intercepted network flows. This will likely be initially empty.
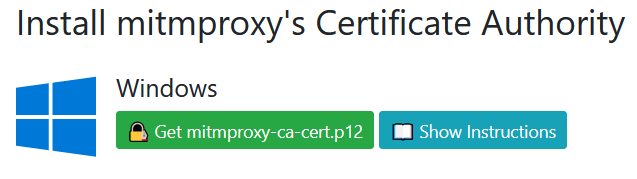
In order to intercept traffic, mitmproxy needs to install a root certificate. Once mitmweb.exe is running, navigate to mitm.it. If everything is working as expected, there should be options to install the mitmproxy certificate for various operating systems and devices.
After the certificate is installed, the proxy should be fully set up. You can restart mitmweb.exe and observe some traffic being intercepted.
At this point, the proxy is verified as working. You can try to launch the game and begin inspecting traffic. However, if you do that, you will notice that no traffic is coming through. The game will appear to be working fine: it will log in to the network, display messages, show available lobbies, and function just as before. This means that the game’s traffic is not being routed through the proxy that we set up.
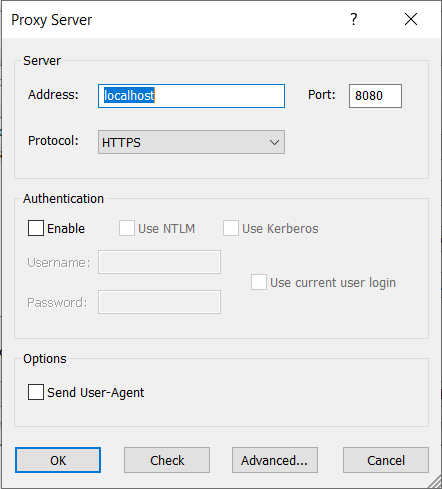
This might seem like a big roadblock, but fear not. There are multiple tools that configure applications to run through a proxy. For this I used Proxifier, which is paid software but provides a free 30-day trial. After installing and launching Proxifier, configure the HTTPS proxy by navigating to Profile -> Proxy Servers…
In this prompt, fill in the address of the HTTPS proxy that was set up with mitmproxy.
Once this is done, traffic of every application will be routed through the mitmproxy. To verify, you can launch the game again and look in the mitmproxy tab. You should now see the various APIs that get called from within the game in their unencrypted form.
From here on, you can begin interacting with the game and seeing what messages are sent to the server as a result of your actions. Doing so will allow you to discover more APIs, and you can begin to get a better picture of how the client-server interaction drives what you see in the game. Once you are done monitoring the traffic, you can shut down Proxifier, mitmproxy, and disable the manual proxy settings in Windows.
This concludes the easy way to reverse engineer REST APIs: through the combination of a couple of tools we are able to quickly see the requests and responses that are being sent, even if TLS is being used. The rest of this series will focus on reverse engineering the game itself to get the unencrypted request and response payloads.